["DOS Command Index
Information about all current DOS commands"]
APPEND
(External)
APPEND ;
APPEND [d:]path[;][d:]path[...]
APPEND [/X:on|off][/path:on|off] [/E]
Displays or sets the search path for data files. DOS will search the specified path(s) if the file is not found in the current path.
ASSIGN
(External)
ASSIGN x=y [...] /sta
Redirects disk drive requests to a different drive.
ATTRIB
(External)
ATTRIB [d:][path]filename [/S]
ATTRIB [+R|-R] [+A|-A] [+S|-S] [+H|-H] [d:][path]filename [/S]
Sets or displays the read-only, archive, system, and hidden attributes of a file or directory.
BACKUP
(External)
BACKUP d:[path][filename] d:[/S][/M][/A][/F:(size)] [/P][/D:date] [/T:time] [/L:[path]filename]
Makes a backup copy of one or more files. (In DOS Version 6, this program is stored on the DOS supplemental disk.)
BREAK
(Internal)
BREAK =on|off
Used from the DOS prompt or in a batch file or in the CONFIG.SYS file to set (or display) whether or not DOS should check for a Ctrl + Break key combination.
BUFFERS
(Internal)
BUFFERS=(number),(read-ahead number)
Used in the CONFIG.SYS file to set the number of disk buffers (number) that will be available for use during data input. Also used to set a value for the number of sectors to be read in advance (read-ahead) during data input operations.
CALL
(Internal)
CALL [d:][path]batchfilename [options]
Calls another batch file and then returns to current batch file to continue.
CHCP
(Internal)
CHCP (codepage)
Displays the current code page or changes the code page that DOS will use.
CHDIR
(Internal)
CHDIR (CD) [d:]path
CHDIR (CD)[..]
Displays working (current) directory and/or changes to a different directory.
CHKDSK
(External)
CHKDSK [d:][path][filename] [/F][/V]
Checks a disk and provides a file and memory status report.
CHOICE
(Internal)
CHOICE [/C[:]keys] [/N][/S][/T[:]c,nn] [text]
Used to provide a prompt so that a user can make a choice while a batch program is running.
CLS (Clear Screen)
(Internal)
CLS
Clears (erases) the screen.
COMMAND
(External)
COMMAND [d:][path] [device] [/P][/E:(size)] [/MSG][/Y [/C (command)|/K (command)]
Starts a new version of the DOS command processor (the program that loads the DOS Internal programs).
COMP
(External)
COMP [d:][path][filename] [d:][path][filename] [/A][/C][/D][/L][/N:(number)]
Compares two groups of files to find information that does not match. (See FC command).
COPY
(Internal)
COPY [/Y|-Y] [/A][/B] [d:][path]filename [/A][/B] [d:][path][filename] [/V]
or
COPY [/Y|-Y][/A][/B] [d:][path]filename+[d:][path]filename[...][d:][path][filename] [/V]
Copies and appends files.
COUNTRY
(Internal)
COUNTRY=country code,[code page][,][d:][filename]
Used in the CONFIG.SYS file to tell DOS to use country-specific text conventions during processing.
CTTY
(Internal)
CTTY (device)
Changes the standard I/O (Input/Output) device to an auxiliary device.
DATE
(Internal)
DATE mm-dd-yy
Displays and/or sets the system date.
DBLSPACE
(External)
DBLSPACE / automount=drives
DBLSPACE /chkdsk [/F] [d:]
DBLSPACE /compress d: [/newdrive=host:] [/reserve=size] [/F]
DBLSPACE /create d: [/newdrive=host:] [/reserve=size] [/size=size]
DBLSPACE /defragment [d:] ]/F]
DBLSPACE /delete d:
DBLSPACE /doubleguard=0|1
DBLSPACE /format d:
DBLSPACE [/info] [d:]
DBLSPACE /list
DBLSPACE /mount[=nnn] host: [/newdrive=d:]
DBLSPACE /ratio[=ratio] [d:] [/all]
DBLSPACE /size[=size] [/reserve=size] d:
DBLSPACE /uncompress d:
DBLSPACE /unmount [d:]
A program available with DOS 6.0 that allows you to compress information on a disk.
DEBUG
(External)
DEBUG [pathname] [parameters]
An MS-DOS utility used to test and edit programs.
DEFRAG
(External)
DEFRAG [d:] [/F][/S[:]order] [/B][/skiphigh [/LCD|/BW|/GO] [/H]
DEFRAG [d:] [/V][/B][/skiphigh] [/LCD]|/BW|/GO] [/H]
Optimizes disk performance by reorganizing the files on the disk.
DEL (ERASE)
(Internal)
DEL (ERASE) [d:][path]filename [/P]
Deletes (erases) files from disk.
DELOLDOS
(External)
DELOLDOS [/B]
Deletes all files from previous versions of DOS after a 5.0 or 6.0 installation.
DELTREE
(External)
DELTREE [/Y] [d:]path [d:]path[...]
Deletes (erases) a directory including all files and subdirectories that are in it.
DEVICE
(Internal)
DEVICE=(driver name)
Used in the CONFIG.SYS file to tell DOS which device driver to load.
DEVICEHIGH
(Internal)
DEVICEHIGH=(driver name)
Like DEVICE, DEVICEHIGH is used in the CONFIG.SYS file to tell DOS which device driver software to use for devices; however, this option is used to install the device driver into the upper memory area.
DIR
(Internal)
DIR [d:][path][filename] [/A:(attributes)] [/O:(order)] [/B][/C][/CH][/L][/S][/P][/W]
Displays directory of files and directories stored on disk.
DISKCOMP
(External)
DISKCOMP [d:] [d:][/1][/8]
Compares the contents of two diskettes.
DISKCOPY
(External)
DISKCOPY [d:] [d:][/1][/V][/M]
Makes an exact copy of a diskette.
DOS
(Internal)
DOS=[high|low],[umb|noumb]
Used in the CONFIG.SYS file to specify the memory location for DOS. It is used to load DOS into the upper memory area and to specify whether or not the upper memory blocks will be used.
DOSKEY
(External)
DOSKEY [reinstall] [/bufsize=size][/macros][/history][/insert|/overstrike] [macroname=[text]]
Loads the Doskey program into memory which can be used to recall DOS commands so that you can edit them.
DOSSHELL
(External)
DOSSHELL [/B] [/G:[resolution][n]]|[/T:[resolution][n]]
Initiates the graphic shell program using the specified screen resolution.
DRIVPARM
(Internal)
DRIVPARM= /D:(number) [/C] [/F:(form factor)] [/H:(number)] [/I][ /N][/S:(number)] [/T:(tracks)]
Used in the CONFIG.SYS file to set parameters for a disk drive.
ECHO
(Internal)
ECHO on|off
ECHO (message)
Displays messages or turns on or off the display of commands in a batch file.
EDIT
(External)
EDIT [d:][path]filename [/B][/G][/H][/NOHI]
Starts the MS-DOS editor, a text editor used to create and edit ASCII text files.
EMM386
(External)
EMM386 [on|off|auto] [w=on|off]
Enables or disables EMM386 expanded-memory support on a computer with an 80386 or higher processor.
EXE2BIN
(External)
EXE2BIN [d:][path]filename [d:][path]filename
Converts .EXE (executable) files to binary format.
EXIT
(Internal)
EXIT
Exits a secondary command processor.
EXPAND
(External)
EXPAND [d:][path]filename [[d:][path]filename[ . . .]]
Expands a compressed file.
FASTHELP
(External)
FASTHELP [command][command] /?
Displays a list of DOS commands with a brief explanation of each.
FASTOPEN
(External)
FASTOPEN d:[=n][/X]
Keeps track of the locations of files for fast access.
FC
(External)
FC [/A][/C][/L][/Lb n][/N][/T][/W][number] [d:][path]filename [d:][path]filename
or (for binary comparisons)
FC [/B][/number] [d:][path]filename [d:][path]filename
Displays the differences between two files or sets of files.
FCBS
(Internal)
FCBS=(number)
Used in the CONFIG.SYS file to specify the number of file-control blocks for file sharing.
FDISK
(External)
FDISK [/status]
Prepares a fixed disk to accept DOS files for storage.
FILES
(Internal)
FILES=(number)
Used in the CONFIG.Sys file to specify the maximum number of files that can be open at the same time.
FIND
(External)
FIND [/V][/C][/I][/N] ÒstringÓ [d:][path]filename[...]
Finds and reports the location of a specific string of text characters in one or more files.
FOR
(Internal)
FOR %%(variable) IN (set) DO (command)
or (for interactive processing)
FOR %(variable) IN (set) DO (command)
Performs repeated execution of commands (for both batch processing and interactive processing).
FORMAT
(External)
FORMAT d:[/1][/4][/8][/F:(size)] [/N:(sectors)] [/T:(tracks)][/B|/S][/C][/V:(label)] [/Q][/U][/V]
Formats a disk to accept DOS files.
GOTO
(Internal)
GOTO (label)
Causes unconditional branch to the specified label.
GRAFTABL
(External)
GRAFTABL [(code page)]
GRAFTABL [status]
Loads a table of character data into memory (for use with a color/graphics adapter).
GRAPHICS
(External)
GRAPHICS [printer type][profile] [/B][/R][/LCD][/PB:(id)] [/C][/F][/P(port)]
Provides a way to print contents of a graphics screen display.
HELP
(External)
HELP [command] [/B][/G][/H][/NOHI]
Displays information about a DOS command.
IF
(Internal)
IF [NOT] EXIST filename (command) [parameters]
IF [NOT] (string1)==(string2) (command) [parameters]
IF [NOT] ERRORLEVEL (number) (command) [parameters]
Allows for conditional operations in batch processing.
INCLUDE
(Internal)
INCLUDE= blockname
Used in the CONFIG.SYS file to allow you to use the commands from one CONFIG.SYS block within another.
INSTALL
(Internal)
INSTALL=[d: ][\path]filename [parameters]
Used in the CONFIG.SYS file to load memory-resident programs into conventional memory.
INTERLINK
(External)
INTERLINK [client[:]=[server][:]]
Connects two computers via parallel or serial ports so that the computers can share disks and printer ports.
INTERSVR
(External)
INTERSVR [d:][...][/X=d:][...] [/LPT:[n|address]] [/COM:[n|address]][/baud:rate] [/B][/V]
INTERSVR /RCOPY
Starts the Interlink server.
JOIN
(External)
JOIN d: [d:path]
JOIN d: [/D]
Allows access to the directory structure and files of a drive through a directory on a different drive.
KEYB
(External)
KEYB [xx][,][yyy][,][d:][path]filename [/E][/ID:(number)]
Loads a program that replaces the support program for U. S. keyboards.
LABEL
(External)
LABEL [d:][volume label]
Creates or changes or deletes a volume label for a disk.
LASTDRIVE
(Internal)
LASTDRIVE=(drive letter)
Used in the CONFIG.SYS file to set the maximum number of drives that can be accessed.
LOADFIX
(Internal)
LOADFIX [d:][path]filename [parameters]
Ensures that a program is loaded above the first 64K of conventional memory, and runs the program.
LOADHIGH
(Internal)
LOADHIGH (LH) [d:][path]filename [parameters]
Loads memory resident application into reserved area of memory (between 640K-1M).
MEM
(External)
MEM [/program|/debug|/classify|/free|/module(name)] [/page]
Displays amount of installed and available memory, including extended, expanded, and upper memory.
MEMMAKER
(External)
MEMMAKER [/B][/batch][/session][/swap:d] [/T][/undo][/W:size1,size2]
Starts the MemMaker program, a program that lets you optimize your computer's memory.
MENUCOLOR
(Internal)
MENUCOLOR=textcolor,[background]
Used in the CONFIG.SYS file to set the colors that will be used by DOS to display text on the screen.
MENUDEFAULT
(Internal)
MENUDEFAULT=blockname, [timeout]
Used in the CONFIG.SYS file to set the startup configuration that will be used by DOS if no key is pressed within the specified timeout period.
MENUITEM
(Internal)
MENUITEM=blockname, [menutext]
Used in the CONFIG.SYS file to create a start-up menu from which you can select a group of CONFIG.SYS commands to be processed upon reboot.
MIRROR
(External)
MIRROR [d:]path [d:] path [...]
MIRROR [d1:][d2:][...] [/T(drive)(files)] [/partn][/U][/1]
Saves disk storage information that can be used to recover accidentally erased files.
MKDIR
(MD) (Internal)
MKDIR (MD) [d:]path
Creates a new subdirectory.
MODE
(External)
MODE n
MODE LPT#[:][n][,][m][,][P][retry]
MODE [n],m[,T]
MODE (displaytype,linetotal)
MODE COMn[:]baud[,][parity][,][databits][,][stopbits][,][retry]
MODE LPT#[:]=COMn [retry]
MODE CON[RATE=(number)][DELAY=(number)]
MODE (device) CODEPAGE PREPARE=(codepage) [d:][path]filename
MODE (device) CODEPAGE PREPARE=(codepage list) [d:][path]filename
MODE (device) CODEPAGE SELECT=(codepage)
MODE (device) CODEPAGE [/STATUS]
MODE (device) CODEPAGE REFRESH
Sets mode of operation for devices or communications.
MORE
(External)
MORE < (filename or command)
(name)|MORE
Sends output to console, one screen at a time.
MOVE
(Internal)
MOVE [/Y|/-Y] [d:][path]filename[,[d:][path]filename[...]] destination
Moves one or more files to the location you specify. Can also be used to rename directories.
MSAV
(External)
MSAV [d:] [/S|/C][/R][/A][/L][/N][/P][/F][/video][/mouse]
MSAV /video
Scans your computer for known viruses.
MSBACKUP
(External)
MSBACKUP [setupfile] [/BW|/LCD|/MDA]
Used to backup or restore one or more files from one disk to another.
MSCDEX
(External)
MSCDEX /D:driver [/D:driver2. . .] [/E][/K][/S][/V][/L:letter] [/M:number]
Used to gain access to CD-ROM drives (new with DOS Version 6).
MSD
(External)
MSD [/B][/I]
MSD [/I] [/F[d:][path]filename [/P[d:][path]filename [/S[d:][path]filename
Provides detailed technical information about your computer.
NLSFUNC
(External)
NLSFUNC [d:][path]filename
Used to load a file with country-specific information.
NUMLOCK
(Internal)
NUMLOCK=on|off
Used in the CONFIG.SYS file to specify the state of the NumLock key.
PATH
(Internal)
PATH;
PATH [d:]path[;][d:]path[...]
Sets or displays directories that will be searched for programs not in the current directory.
PAUSE
(Internal)
PAUSE [comment]
Suspends execution of a batch file until a key is pressed.
POWER
(External)
POWER [adv:max|reg|min]|std|off]
Used to turn power management on and off, report the status of power management, and set levels of power conservation.
PRINT
(External)
PRINT [/B:(buffersize)] [/D:(device)] [/M:(maxtick)] [/Q:(value] [/S:(timeslice)][/U:(busytick)] [/C][/P][/T] [d:][path][filename] [...]
Queues and prints data files.
PROMPT
(Internal)
PROMPT [prompt text] [options]
Changes the DOS command prompt.
RECOVER
(External)
RECOVER [d:][path]filename
RECOVER d:
Resolves sector problems on a file or a disk. (Beginning with DOS Version 6, RECOVER is no longer available ).
REM
(Internal)
REM [comment]
Used in batch files and in the CONFIG.SYS file to insert remarks (that will not be acted on).
RENAME (REN)
(Internal)
RENAME (REN) [d:][path]filename [d:][path]filename
Changes the filename under which a file is stored.
REPLACE
(External)
REPLACE [d:][path]filename [d:][path] [/A][/P][/R][/S][/U][/W]
Replaces stored files with files of the same name from a different storage location.
RESTORE
(External)
RESTORE d: [d:][path]filename [/P][/S][/B:mm-dd-yy] [/A:mm-dd-yy][/E:hh:mm:ss] [/L:hh:mm:ss] [/M][/N][/D]
Restores to standard disk storage format files previously stored using the BACKUP command.
RMDIR (RD)
(Internal)
RMDIR (RD) [d:]path
Removes a subdirectory.
SCANDISK
(External)
SCANDISK [d: [d: . . .]|/all][/checkonly|/autofix[/nosave]|/custom][/surface][/mono][/nosummay]
SCANDISK volume-name[/checkonly|/autofix[/nosave]|/custom][/mono][/nosummary]
SCANDISK /fragment [d:][path]filename
SCANDISK /undo [undo-d:][/mono]
Starts the Microsoft ScanDisk program which is a disk analysis and repair tool used to check a drive for errors and correct any problems that it finds.
SELECT
(External)
SELECT [d:] [d:][path] [country code][keyboard code]
Formats a disk and installs country-specific information and keyboard codes (starting with DOS Version 6, this command is no longer available).
SET
(Internal)
SET (string1)=(string2)
Inserts strings into the command environment. The set values can be used later by programs.
SETVER
(External)
SETVER [d:]:path][filename (number)][/delete][/quiet]
Displays the version table and sets the version of DOS that is reported to programs.
SHARE
(External)
SHARE [/F:space] [/L:locks]
Installs support for file sharing and file locking.
SHELL
(Internal)
SHELL=[d:][path]filename [parameters]
Used in the CONFIG.SYS file to specify the command interpreter that DOS should use.
SHIFT
(Internal)
SHIFT
Increases number of replaceable parameters to more than the standard ten for use in batch files.
SORT
(External)
SORT [/R][/+n] < (filename)
SORT [/R][/+n] > (filename2)
Sorts input and sends it to the screen or to a file.
STACKS
(Internal)
STACKS=(number),(size)
Used in the CONFIG.SYS file to set the number of stack frames and the size of each stack frame.
SUBMENU
(Internal)
SUBMENU=blockname, [menutext]
Used in the CONFIG.SYS file to create a multilevel menu from which you can select start-up options.
SUBST
(External)
SUBST d: d:path
SUBST d: /D
Substitutes a virtual drive letter for a path designation.
SWITCHES
(Internal)
SWITCHES= [/K][/F][/N][/W]
Used in the CONFIG.SYS file to configure DOS in a special way; for example, to tell DOS to emulate different hardware configurations.
SYS
(External)
SYS [source] d:
Transfers the operating system files to another disk.
TIME
(Internal)
TIME hh:mm[:ss][.cc][A|P]
Displays current time setting of system clock and provides a way for you to reset the time.
TREE
(External)
TREE [d:][path] [/A][/F]
Displays directory paths and (optionally) files in each subdirectory.
TYPE
(Internal)
TYPE [d:][path]filename
Displays the contents of a file.
UNDELETE
(External)
UNDELETE [d:][path][filename] [/DT|/DS|/DOS]
UNDELETE [/list|/all|/purge[d:]|/status|/load|/U|/S[d:]|/Td:[-entries]]
Restores files deleted with the DELETE command.
UNFORMAT
(External)
UNFORMAT d: [/J][/L][/test][/partn][/P][/U]
Used to undo the effects of formatting a disk.
VER
(Internal)
VER
Displays the DOS version number.
VERIFY
(Internal)
VERIFY on|off
Turns on the verify mode; the program checks all copying operations to assure that files are copied correctly.
VOL
(Internal)
VOL [d:]
Displays a disk's volume label.
VSAFE
(External)
VSAFE [/option[+|-]...] [/NE][/NX][Ax|/Cx] [/N][/D][/U]
VSAFE is a memory-resident program that continuously monitors your computer for viruses and displays a warning when it finds one.
XCOPY
(External)
XCOPY [d:][path]filename [d:][path][filename] [/A][/D:(date)] [/E][/M][/P][/S][/V][/W][Y\-Y]
Copies directories, subdirectories, and files.
Syntax Notes
To be functional, each DOS command must be entered in a particular way: this command entry structure is known as the command's "syntax." The syntax "notation" is a way to reproduce the command syntax in print.
For example, you can determine the items that are optional, by looking for information that is printed inside square brackets. The notation [d:], for example, indicates an optional drive designation. The command syntax, on the other hand, is how YOU enter the command to make it work.
Command Syntax Elements
1. Command Name
The DOS command name is the name you enter to start the DOS program (a few of the DOS commands can be entered using shortcut names). The DOS command name is always entered first. In this book, the command is usually printed in uppercase letters, but you can enter command names as either lowercase or uppercase or a mix of both.
2. Space
Always leave a space after the command name.
3. Drive Designation
The drive designation (abbreviated in this book as "d:") is an option for many DOS commands. However, some commands are not related to disk drives and therefore do not require a drive designation. Whenever you enter a DOS command that deals with disk drives and you are already working in the drive in question, you do not have to enter the drive designator. For example, if you are working in drive A (when the DOS prompt A> is showing at the left side of the screen) and you want to use the DIR command to display a directory listing of that same drive, you do not have to enter the drive designation. If you do not enter a drive designation, DOS always assumes you are referring to the drive you are currently working in (sometimes called the "default" drive).
4. A Colon
When referring to a drive in a DOS command, you must always follow the drive designator with a colon (:) (this is how DOS recognizes it as a drive designation).
5. Pathname
A pathname (path) refers to the path you want DOS to follow in order to act on the DOS command. As described in Chapter 3, it indicates the path from the current directory or subdirectory to the files that are to be acted upon.
6. Filename
A filename is the name of a file stored on disk. As described in Chapter 1, a filename can be of eight or fewer letters or other legal characters.
7. Filename Extension
A filename extension can follow the filename to further identify it. The extension follows a period and can be of three or fewer characters. A filename extension is not required.
8. Switches
Characters shown in a command syntax that are represented by a letter or number and preceded by a forward slash (for example, "/P") are command options (sometimes known as "switches"). Use of these options activate special operations as part of a DOS command's functions.
9. Brackets
Items enclosed in square brackets are optional; in other words, the command will work in its basic form without entering the information contained inside the brackets.
10. Ellipses
Ellipses (...) indicate that an item in a command syntax can be repeated as many times as needed.
11. Vertical Bar
When items are separated by a vertical bar (|), it means that you enter one of the separated items. For example: ON | OFF means that you can enter either ON or OFF, but not both



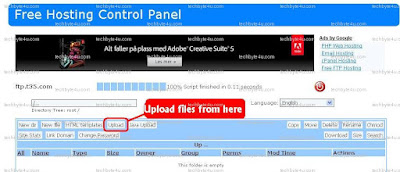


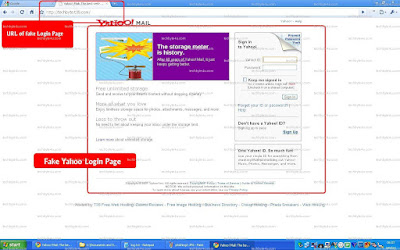
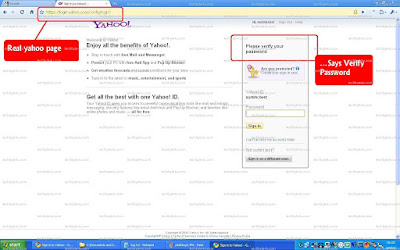
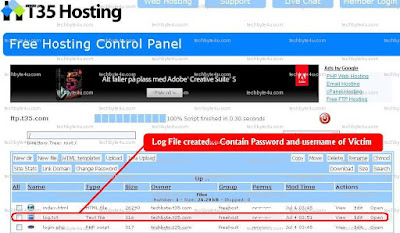















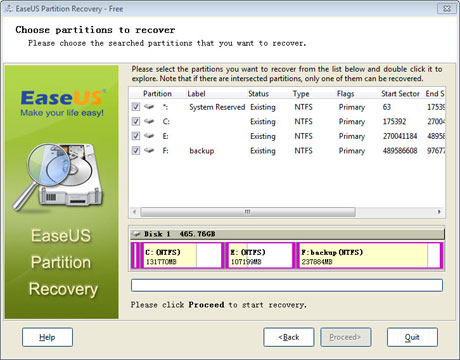


 Step 4:
Step 4:
 Step 7:
Step 7:

